What is WebAssembly?
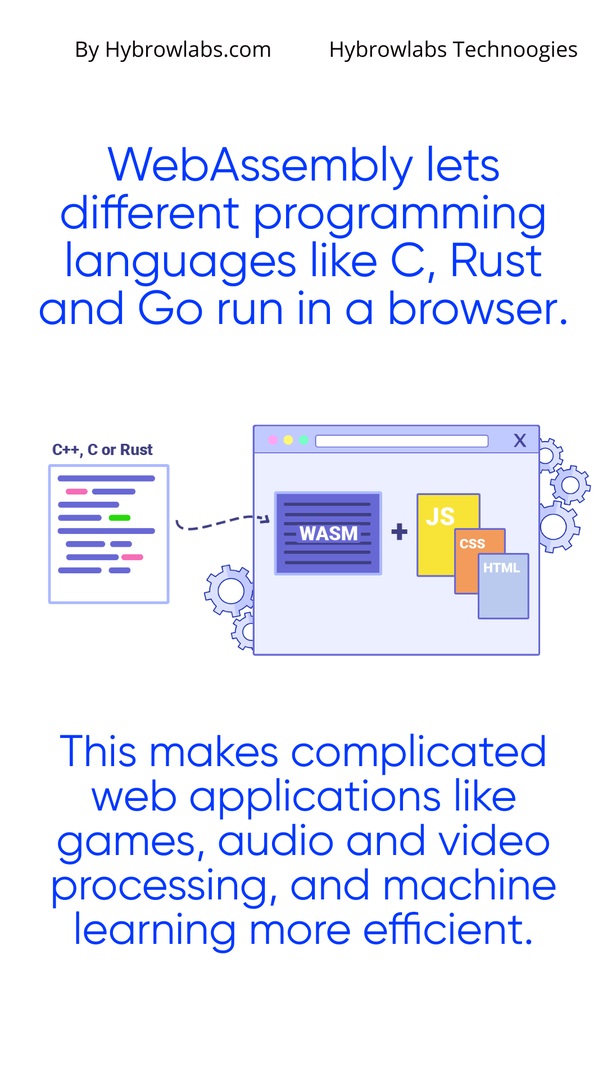
WebAssembly revolutionized the development of web-based software. This binary format allows programs written in various programming languages such as C, Rust and Go to run in a browser environment. WebAssembly does this by providing a low-level virtual machine that performs better than plain JavaScript, which is typically interpreted at runtime. Computationally intensive applications that were previously difficult to run on web platforms, such as games, audio and video processing, and machine learning, are now perfectly suited to WebAssembly due to its efficiency.
Wasm, sometimes called WebAssembly, is a low-level bytecode format designed to run in current browsers. It is a cross-platform technology that can be used on a wide range of devices, including desktop computers, mobile phones and Internet of Things (IoT) devices. WebAssembly, a language that works faster and more efficiently than JavaScript despite being a high-level language, is more like an assembly.
How does Web Assembly work?

Sandbox environments are intended for the execution of WebAssembly. It indicates that it is separate from the other website elements and cannot communicate with them or the user's computer. Moreover, it is intended to be safer than other web technologies like JavaScript.
Code written in higher-level programming languages like C++, Rust, or Go translated into WebAssembly. The user's browser receives the compiled code, which is then executed in a sandboxed environment. The code can't access other areas of the browser or the user's machine since it runs in a distinct memory space.
Overview of Security Concerns
Although WebAssembly has numerous benefits for web development, and it provides new security problems. It is vulnerable to repetition attacks like buffer overflows, integer overflows, and type confusion due to the language's low-level and direct memory access capabilities. In addition, it is possible to carry out malicious code on the user's device because WebAssembly modules can be automatically loaded and carried out in the browser.
A sandboxed execution environment, memory safety guarantees, and a verification system that assures that only legitimate WebAssembly code is executed are just a few of the security measures that WebAssembly contains to alleviate these worries. Moreover, web browsers employ security controls like Same-Origin Policy and Content Security Policy to stop malicious malware from accessing private data or running arbitrary code. Developers must adhere to recommended secure code and deployment practices and be aware of the security implications of utilizing WebAssembly.
Strong hardware-enforced isolation, software sandboxing, and runtime safety checks are part of web assembly's security approach, which guards against various security risks. Protection from memory safety violations, type safety violations, and other security concerns is offered by the WebAssembly sandbox.
How Can WebAssembly Benefit You?

1. Improved Performance
Compared to more established web technologies like JavaScript, WebAssembly offers significant performance improvements. JavaScript, an interpreted language, can run substantially slower than WebAssembly since it is compiled into machine code. Creating complicated and resource-intensive apps like games, video and audio processing and scientific simulations that would have been impossible to build solely with JavaScript is now possible thanks to the ability to design online applications with nearly-native speed.
2. Cross-platform compatibility
It is easier for developers to design and make web applications available that can run on different devices and operating systems because the web configuration can work on different platforms and architectures. Therefore, developers can write their code just once and publish it on multiple platforms without worrying about platform compatibility or optimization.
3. Reduction in Payload Size
WebAssembly modules are binary files that can be packaged more efficiently than text-based web technologies such as JavaScript or HTML. Web applications can be significantly scaled down, which would speed up loading and consume less bandwidth. Performance improvements and latency reductions are possible because WebAssembly modules can be loaded and executed simultaneously.
4. Portability
Integrating WebAssembly into current web applications is simply because it is made to be interoperable with other web technologies, like HTML and JavaScript. As a result, developers can convert existing programmes to WebAssembly progressively rather than starting from scratch. Additionally, developers can use WebAssembly with various programming languages to select the one that best meets their requirements and tastes.
WebAssembly Risks Unveiled: Is Your System Vulnerable to These Impending Threats?

WebAssembly provides various advantages for web development but also introduces some security risks. Some potential risks include the following:
1. Malware
Side-channel attacks that take advantage of underlying software or hardware flaws can be carried out by WebAssembly code.
2. Resource abuse
WebAssembly can create code that consumes excessive resources like CPU cycles or memory, leading to system slowdowns or crashes.
3. Attack surface
Web assembly increases the attack surface of web applications, providing another entry point for attackers to exploit vulnerabilities in the code.
4. Side-channel attacks
WebAssembly code can perform side-channel attacks that exploit underlying hardware or software weaknesses.
5. Denial of Service attacks
WebAssembly code can launch denial-of-service attacks against web servers and other targets.
What are the Top Security Concerns You Need to Know?
1. Code Execution Vulnerabilities
Code written with WebAssembly can introduce fresh code execution-related security flaws such as buffer overflows, integer overflows, and type misunderstanding attacks. It is because WebAssembly code has direct memory access and can interact with system resources in ways that attackers could take advantage of. Malicious actors may leverage these flaws to breach a user's device's security, which could lead to data loss, unauthorized code execution, or other negative outcomes.
2. Information Leaks and Privacy Concerns
When used by malicious code, WebAssembly can access private data on a user's device, including the camera, microphone, and location. It poses a privacy concern. Moreover, security flaws in the operating system or browser could expose confidential data like passwords. WebAssembly contains built-in security protections such as a sandboxed execution environment, memory safety guarantees, and a verification mechanism to ensure only legitimate code runs to address these security issues. Moreover, web browsers employ security controls like Same-Origin Policy and Content Security Policy to stop malicious malware from accessing private data or running arbitrary code. Developers must, meanwhile, be on the lookout for security vulnerabilities and adhere to best practices for secure code and deployment.
Bulletproof Your Web Assembly: What Are the Essential Security Measures You Must Implement?
1. Code Validation and Verification
WebAssembly aims to provide a secure and reliable platform for running code on the web. Code validation and verification procedures are one of the most important security measures, as they ensure that executable code is safe and error-free. Code written in WebAssembly is checked for conformance before it is run to prevent memory corruption, type confusion, and other security problems.
2. Sandboxing
Sandboxing is another important security mechanism in WebAssembly. A process called sandboxing isolates code execution within a regulated setting, preventing it from having access to system resources or data that it shouldn't. Because WebAssembly code is run in a sandboxed environment, it cannot access private information or host system resources.
3. Memory Isolation
Another crucial security measure in WebAssembly is memory segregation. WebAssembly code cannot access or modify memory outside its own sandboxed environment since it runs in a different memory space from the host system. By doing this, attackers are less likely to be able to take advantage of memory-related vulnerabilities such as buffer overflows.
4. Authentication and Authorization
Applications written in WebAssembly can also utilize authentication and authorization techniques to manage user access to resources and information. You can accomplish this using common online authentication methods like OAuth or OpenID Connect or by implementing unique authentication and permission techniques directly within the WebAssembly application. WebAssembly apps can help to prevent unwanted access and guard against attacks by limiting access to important resources and data.
What Are the Best Practices for Top-Notch Security?
1. Secure Deployment
Applications built using WebAssembly should be set up in a safe environment with suitable firewalls and access controls to guard against unauthorized access. To avoid data interceptions and eavesdropping, applications should be set up to use secure transport protocols like HTTPS.
2. Regular Updates and Patches
Like all software, WebAssembly programmes should be regularly updated and patched to fix known issues and guarantee security. Developers should follow security bulletins and news feeds to keep up with new threats and vulnerabilities.
3. Risk Assessment and Mitigation
Developers should do a risk assessment to find potential security risks and vulnerabilities in their WebAssembly apps. It should be done throughout several stages of the development process, such as design, development, testing, and deployment. To address the risks and vulnerabilities that have been identified, risk mitigation methods should be implemented.
4. Security Training for Developers
Developers should take security training to ensure they comprehend the security concerns and recommended practises related to WebAssembly development. Topics, including secure coding methods, threat modelling, risk assessment, and mitigation techniques, should be covered in this programme. Also, to improve the security of their applications, developers should receive training on the usage of security tools and technologies such as encryption and authentication techniques.
Conclusion
A potent technology, WebAssembly provides considerable advantages for online apps regarding performance and portability. Yet security dangers need to be handled, just like with any technology. Developers should adhere to best practices, including code validation, sandboxing, memory segregation, and authentication and authorization, to guarantee the security of WebAssembly apps. They should also concentrate on safe deployment, frequent updates and patches, risk assessment and mitigation, and developer security training.
We may anticipate future developments in WebAssembly security as this relatively young technology gains popularity. Both the creation of new security tools and technologies and the improvement of current security measures may fall under this category.
To ensure the security of your WebAssembly apps, you can seek the help of professional services such as Hybrowlabs WebAssembly Services. Developers should take security seriously and follow suggested methods as WebAssembly becomes more widely used to protect application security. Furthermore, for WebAssembly to remain a secure platform for web applications, security experts and researchers must continue to improve the state of the art.
FAQs
1. What sets WebAssembly apart from more established web technologies like JavaScript regarding security?
Because it is intended to operate in a sandboxed environment, WebAssembly offers a more secure execution environment than conventional web technologies like JavaScript. As a result, WebAssembly code cannot access resources or data that it shouldn't and is isolated from other system components while being performed in protected memory. Also, before being executed, WebAssembly code is inspected to ensure it complies with guidelines intended to stop memory corruption, type confusion, and other security concerns.
2. Does a sandboxed environment allow WebAssembly code to run without the requirement for additional security measures?
Yes, WebAssembly code is intended to run in a sandboxed environment by default. To maintain the overall security of their WebAssembly apps, developers should still adhere to best practices for safe deployment, frequent updates and patches, risk assessment and mitigation, and security training for developers.
3. Which are webassembly's most prevalent security vulnerabilities, and how may they be reduced?
Buffer overflows, integer overflows, and code injection attacks are some of the most frequent security issues connected with WebAssembly. These risks can be reduced by using best practices like code validation and verification, sandboxing, memory isolation, authentication and authorization, as well as regular updates and patches.
4. Can malicious software be run using WebAssembly on a user's device?
WebAssembly code has the same potential for dangerous virus execution as any other code that runs on a user's device. However, WebAssembly's sandboxed environment, code validation, and verification techniques lessen this risk. Using authentication and authorization techniques to control access to resources and data will help developers further increase the security of their WebAssembly programmes.





a3dc85.jpg)

.jpg)
fd8f11.png)


.jpg)
.jpg)